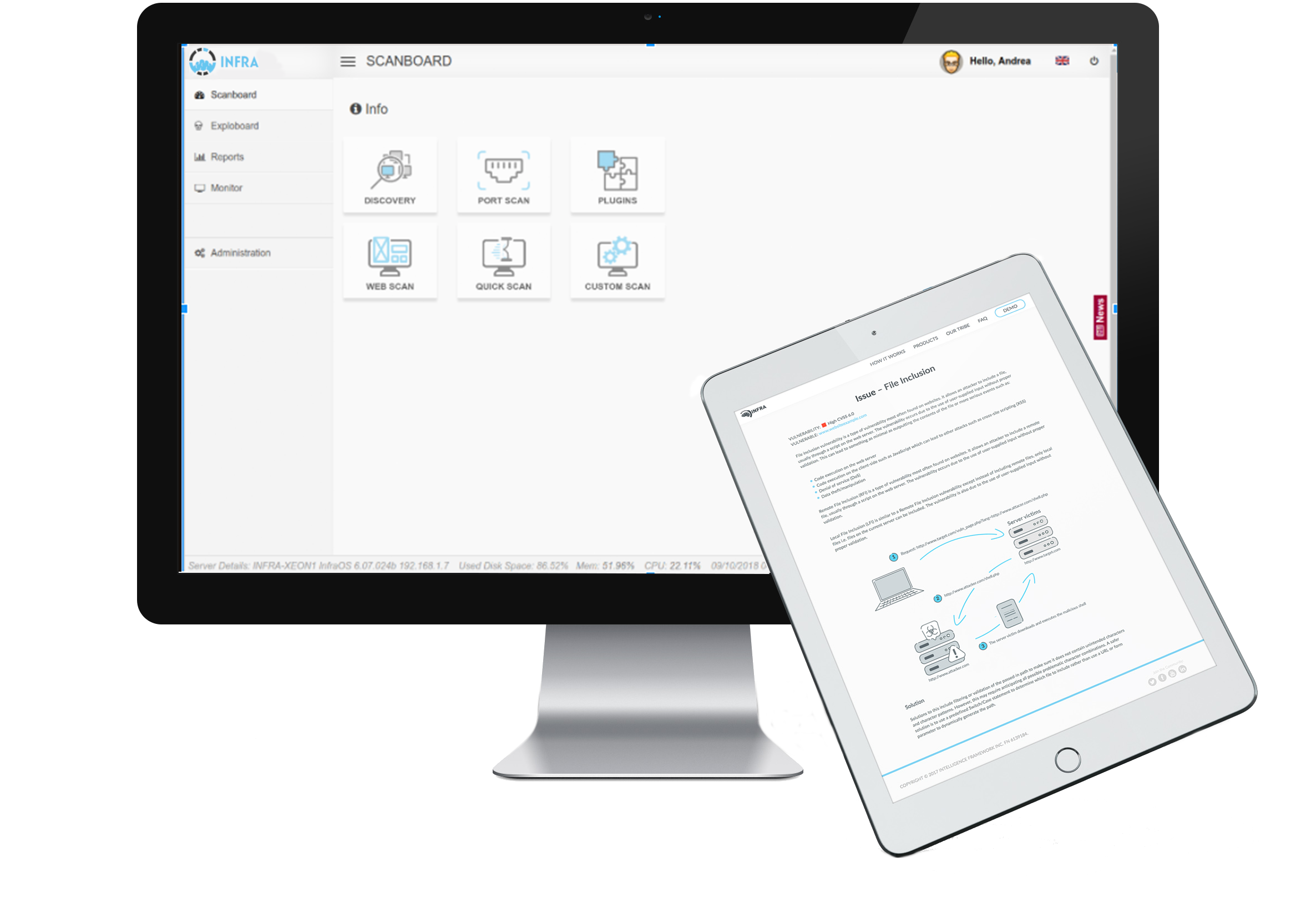
Vulnerability Assessment
The problem is Companies are required to scan for vulnerabilities, scanners rely on databases so they cannot disclose new vulnerabilities, also most of the job still is not automated and is done manually by the analysts, that have to switch between many tools based on signatures (so cannot find undisclosed problems) and have to waste a lot of time exploiting manually.
We build automated solutions that include signature, fuzzing and hacking technologies for Assessment and for Intelligence. Findings more, Verifying more, Automating more, to limit human errors and maximizing reliability. All checks in IoT, servers and web applications are standardized and automated speeding up the vulnerability assessments and the penetration testings...
Let’s automate. VA and PT are mandatory for corporations, but according to Gartner there are only few companies in the market of Vulnerability Assessment and even less in the market of Penetration Testing and IoT security. We find more than them and we Verify more than them. The product is a SECaaS as can be offered as SaaS licensing a device a Virtual Machine or in the Cloud.